
Editorial by:
Alessandro Cortese - Cloud Architect Openwork
No one today can ignore the advantages offered by cloud technologies.
In fact, thanks to the cloud, organizations can enjoy great productivity and flexibility, as well as get all the storage they need to lighten the load on IT departments and, as a result, significant savings on costs originated by server maintenance.
In fact, the Cloud market is growing rapidly.
However, there remain issues that need to be focused on in order to consciously take advantage of all the opportunities of the cloud and in particular we focus here on cybersecurity issues.
There are very effective approaches to protect millions of data from possible threats and attacks: let's talk about Cybersecurity.
More advanced cybersecurity consists of a resilient organizational model
The term "resilience" appears frequently among data protection legal texts, especially now that globally the level of risk is getting higher and higher. Security today must be approached with clarity of mind, pragmatism and above all resilience, with the latter term denoting the ability to overcome a traumatic event in a positive way, by virtue of the fact that a cyber attack involves quite a few traumas.
Resilience and the EU
The European Union's new security strategy is based on resilience and is put in black and white in the Cybersecurity Act, this text aims to create a single security market in terms of products, services and processes among all European countries. In the Cybersecurity Act, the concept of resilience is present as the basis for outlining the entire strategy that would ensure thevanguard of European defenses to deal with new threats. The impetuous and unstoppable growth of the cloud computing market has resulted in the founding of a movement urging standardized security practices in the industry such as the Cloud Security Alliance (CSA): this is a nonprofit association comprising the most important players who are experts in the field, and was formed to spread a higher level of awareness and knowledge among cloud computing users and providers regarding necessary security requirements and attestations of trustworthiness. However, the Cloud Security Alliance is only one of several organizations that have recognized the pressing need to minimize the security risks associated with the adoption of cloud strategies.
Risk as an opportunity
Normal Cybersecurity analyzes the appearance of risks and threats and considers how to reduce or prevent them. The new frontier of cybersecurity also sees these risks as opportunities, which consist of creating a strong network and the drive for continuous improvement; in this network we exchange data and information needed to prevent and combat cyber attacks, and the continuous development encourages bringing in new ideas, investing more without fear of making mistakes.
From reactivity to proactivity
In almost all cases, many companies have demonstrated a purely reactive approach to combating cybercrime; yet, although most cyber attacks on systems are blocked, still a lot of breaches are suffered.
Here reactivity becomes proactivity and cybersecurity becomes cyber-resilience, this means maintaining a proactive behavior, designing and building systems that continue to operate despite attacks, the right strategy also needs the support of all emerging technologies such as: blockchain, artificial intelligence, user behavior analytics and machine learning.
The resilience model
The security resilience model is thus a path to awareness (Security Awareness) of how an organization works based on a high level of collaboration.Doing security is no longer about shutting down and taking cover but proactively and consciously addressing risk.This approach certainly brings together the capabilities of cybersecurity, business continuity and enterprise resilience and involves greater collaboration between areas of the enterprise.
Attention to errors and shared, not diffuse, accountability generate strong responses to weak signals as well as allow for proper planning.
So a resilience plan must be structured along lines of action with clear objectives, priorities, timelines and deadlines. Indications, alerts and proposals for action or improvement are the cornerstone of this action tool, at all levels of the system.
Resilience and best practices
There is no good model of resilience without best practices, every company must produce and activate good security practices, the European Union itself in its Cybersecurity Act calls on organizations to maximize the availability of cyber-security tools for people.
In this, companies and industry players in general must work together, but with particular attention to providers and producers of digital services. It is then the industry that needs to support end users with tools that enable them to take responsibility for their own actions online.
This makes it clear that adherence to best practices and maintaining cyber-security is an indispensable part of the offering to consumers; the gradual spread of the Internet of Things will only increase the front end of companies' exposure to cyber assaults. It is often the sense of alienation that disorients many companies: cyber-security is a prerequisite for growth and development but its evolution often gets out of hand, a certain cultural wall needs to be broken down before investing money in security, and the EU has understood this well, there is no better defense than a resilient mindset and business.
Gartner's Magic Quadrant for distributed infrastructure as a service (IaaS)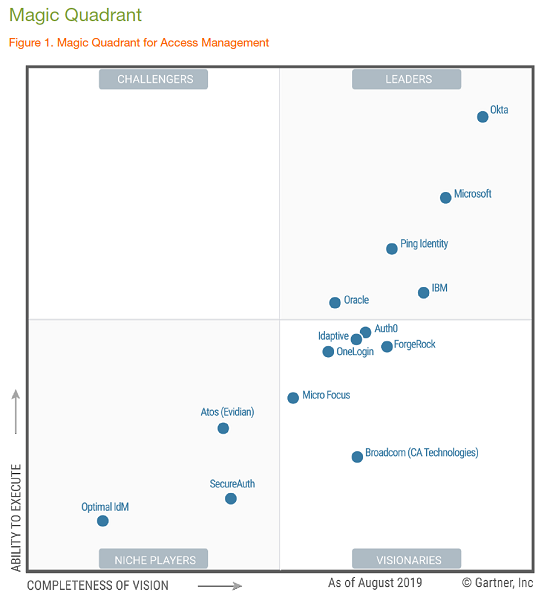
All cloud providers take the issue of security very seriously, well aware that both their customers, partners and prospects are unwilling to accept any level of inefficiency on such a critical point in the cloud world.
Microsoft Azure IaaS where the Jamio Openwork platform services reside has been positioned by Gartner for the sixth consecutive year as a leader in the Magic Quadrant for Cloud Infrastructure as a Service (IaaS), designing services in IaaS to meet all workload needs, offering unique hybrid deployment models tailored to industry-leading levels of security; also supporting open source technologies in the use of various application and administrative tools.
Gartner's comprehensive assessment of IaaS providers covers the strengths, caveats and recommended uses of the leading cloud service providers, one of the foundational points essential to gaining customer trust is security, and Microsoft also demonstrates an awareness of this.
At home in Redmond, a team of more than 3,500 global cyber-security experts is constantly working to ensure the best possible security; there are, of course, also very advanced tools to support the Microsoft team, for example, leveraging machine learning techniques, behavioral analysis and application-based intelligence; data scientists analyze the amount of data available in the Microsoft Intelligent Security Graph; the information obtained provides guidance to services in Azure and helps detect threats more quickly.
Ultimately, cloud customers need to educate themselves about the security policies and procedures of service providers, evaluating the significant cost savings associated with cloud technology that are a strong incentive to outsource some, if not all, of their application needs.
Ignorance is not bliss in the world of cloud computing; data security-not savings-must remain the priority for organizations that choose to enter the world of cloud computing.
Do you also want to try the Zero-Code Jamio?
Puglia Celebrates 50 Years of Digital Development: The InnovaPuglia Event.

A celebratory event organized by InnovaPuglia to mark the 50th anniversary since the founding of C.S.A.T.A. (Center for Studies and Applications in Advanced Technologies) -an entity from which InnovaPuglia descends-was held Nov. 26 in Bari, Italy, at the Villa Romanazzi Carducci Hotel.
The Center for Studies and Applications in Advanced Technologies is a nonprofit association established on Sept. 19, 1969, and is made up of public and private entities, whose founding members were the University of Bari, Bank of Italy, Nuovo Pignone and Formez; the ancestor of InnovaPuglia is thus celebrating 50 years of commitment as a center for research, technology transfer and training in information technology.
Speakers at the event included Salvatore Latronico as President of the Distretto Produttivo dellInformatica Pugliese.
Also present was Piero Cosoli, Senior Program Manager of Openwork as well as Past Director of the Technology & Systems Division of Tecnopolis C.S.A.T.A.
The event was also an opportunity for discussion and reflection on the state of the art of digitization in PA and future innovation projects for the evolution of IT services in the Apulian territory.
The organized event is part of a program carried out by Sole 24ore entitled 'Innovation day: the excellences of the territory" having the purpose of telling and sharing the models of innovation and sustainability that have allowed to generate examples of territorial excellence.
The project included 6 Italian stages: Milan, Bologna, Verona, Naples, Bari and finally Rome.
Happy Holidays from Openwork

Openwork would like to take this opportunity to extend best wishes for a Merry Christmas and a Happy New Year.
Also advises that Customer Service for Jamio openwork customers will remain operational except on December 25 and 26 and January 1, 2020.









